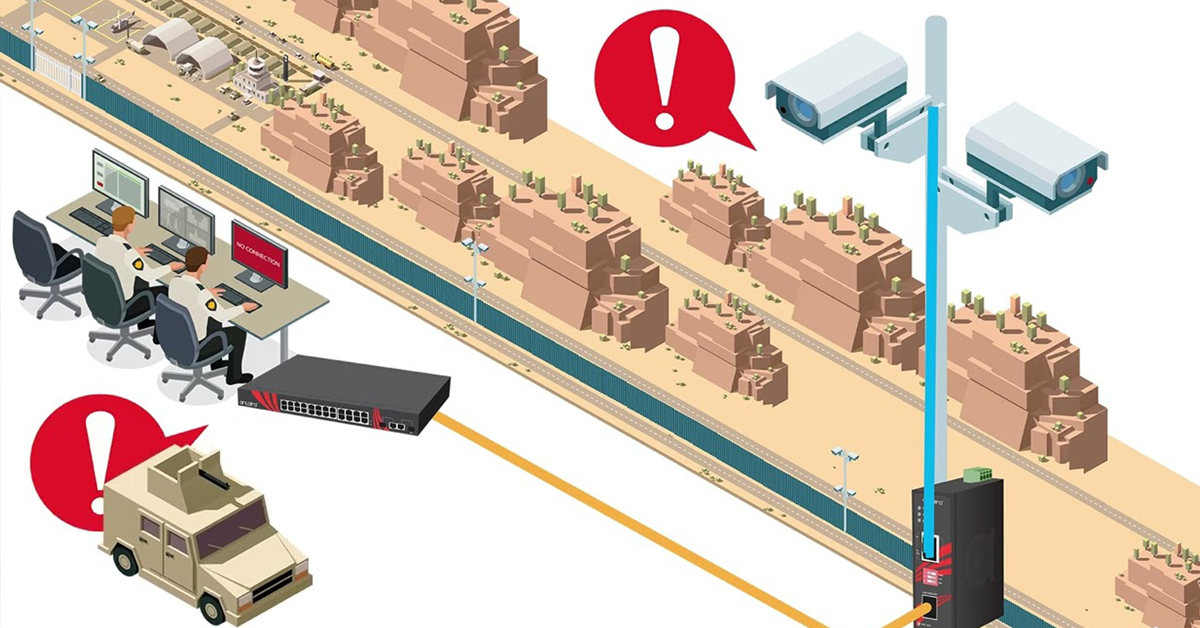
CYBERSECURITY: PROTECTING INDUSTRIAL CONTROL SYSTEMS
Introduction
Industrial control systems are a vital aspect of an industrial network, but they are also extremely vulnerable to outside cyberattacks due to their unprotected design. Like any important network component, it is necessary to invest in proper protective measures to ensure the network’s efficient, undisrupted operation. Below, we will provide information about the importance of protecting industrial control systems, as well as defensive cybersecurity strategies that will help you keep your systems safe from outside influences.
What are Industrial Control Systems?
Industrial control system (ICS) is a collective term that encompasses a variety of control systems and associated instrumentation, such as devices, networks, systems, and controls, for use in industrial process automation or control. Some of the different types of industrial control systems include supervisory control and data acquisition (SCADA) systems, programmable logic controllers (PLC), and distributed control systems (DCS).
The primary purpose of industrial control systems is to streamline business practices that relate to industrial production and mitigate the rate of human error. Industrial control systems are generally most necessary in critical industrial facilities, such as power generation facilities, nuclear plants, or water treatment facilities.
The Importance of Protecting Industrial Control Systems
Since their origin, industrial control networks have grown substantially in terms of their scale as well as their complexity. Originally, such networks were a closed-off, standalone Operational Technology (OT). As such, industrial control systems initially functioned in a controlled area that was heavily isolated.
However, since the emergence of advanced technical developments, such as the Internet of Things (IoT), industrial control networks have developed into rugged, high-speed communication networks. Upon undertaking such development, industrial control networks now require the same type of data link speed and backbone infrastructure as advanced Information Technology (IT) networks. To mandate the Industrial Internet of Things (IIoT) IP based communications, OT networks and IT networks had to converge. The convergence of IT and OT networks provided many benefits for OT networks. For example, it allowed for greater flexibility and control over OT networks, as well as facilitated the creation of more sophisticated OT networks as administrators could take full advantage of IIoT smart devices in terms of increased production, optimized workflow, and expanded communication.
However, the combination of IT and OT networks also brought on additional security concerns for industrial control systems. As previously stated, industrial control systems were designed to operate in isolated, controlled areas and, thus, had very little security. Since the convergence of IT and OT networks, the operation environment of industrial control systems has drastically changed to allow for outside communication. As a result, there is now a need for advanced security measures to protect such vulnerable systems from potential attacks. Below, we will discuss how cybersecurity systems can fulfill this need.
How Cybersecurity Can Help Protect Control Systems
Cybersecurity refers to the protection of the data, hardware, and software of computer systems and networks from theft, damage, disruption, and misdirection. Due to the isolated nature of industrial control systems, the plant managers and engineers who operated them once viewed cybersecurity as trivial and little more than a nuisance. As such, user authentication and access permission settings rarely saw sufficient configuration, and the systems were left unprotected to outside attackers.
Since the convergence of IT and OT networks that allows for outside communication, however, cybersecurity protection measures have become a necessity. Without cybersecurity to prevent unauthorized outside access or influence, vulnerable industrial control systems can fall victim to cyberattackers who seek to gain inside access to critical infrastructures. Over the years, such cyberattacks on unprotected industrial control systems have cost companies hundreds of millions of dollars in revenue due to network downtime.
To avoid joining the millions of people who have experienced the severe consequences of an unprotected industrial control system, a company must invest in cybersecurity management. Due to the increased need for cybersecurity management features, the cybersecurity industry has developed into a specialized field that functions specifically to protect a variety of industrial systems, such as transportation systems and power plants.
Cybersecurity Strategies to Defend Industrial Control Systems
When it comes to protecting your industrial control system, there are a wide variety of cybersecurity strategies that you can implement. Some examples of defense-in-depth cybersecurity measures include:
1. Secure your industrial network devices: The first step in creating a comprehensive cybersecurity plan is to secure the devices in your industrial network. To secure your industrial devices, you should:
- Identify and monitor who can access the devices in your industrial network.
- Require that authorized devices go through verification before they can gain access to your industrial network and proceed to communicate with other devices.
- Increase confidentiality by encrypting configuration data.
- Implement multi-factor authentication when possible.
- Prevent unauthorized access by creating secure password policies that prioritize length over complexity.
- Ensure the integrity of data by encrypting confidential serial interface data.
2. Create a defensible environment: To reduce damage from network perimeter breaches, create a defensible environment by segmenting your networks and restricting host-to-host communication pathways.
3. Regularly monitor the network and respond to threats: To ensure that no new devices link to your network without authorization, monitor your network regularly. Regular monitoring will also help identify any adversarial penetration so that you can quickly execute a prepared response against modern threats. The following monitoring measures are particularly beneficial for protecting your network:
- Monitor IP traffic on ICS boundaries for abnormal or otherwise suspicious communications
- Monitor IP traffic within the control network for the presence of malicious connections or content.
- Implement host-based products to help detect malicious software and identify attack attempts.
- Utilize a login analysis to help identify the use of stolen credentials or improper access, and issue phone calls to verify any anomalies.
- Monitor account and user administration actions to identify any signs of access control manipulation.
Blog Posts

Thermal Camera Selection
How Far Can I See?
How Should Human Temperature Be Measured?

What is Wide Dynamic Range?

MYNOISE AUDIO MIXER REVIEW

WHAT IS A WIRELESS DISTRIBUTION SYSTEM?

POE VS. POE+ VS. POE++: CHOOSING THE RIGHT INDUSTRIAL ETHERNET SWITCH FOR YOU

INDUSTRY-LEADING INDUSTRIAL ETHERNET SWITCHES
UNDERSTANDING WHAT THE INDUSTRIAL INTERNET OF THINGS IS
THE DIFFERENCE BETWEEN A HUB, SWITCH, & ROUTER

5 Benefits of Thermal Imaging Cameras

DIFFERENCE BETWEEN INDUSTRIAL ETHERNET AND REGULAR ETHERNET

INDUSTRIAL NETWORKING EQUIPMENT USED FOR AUTONOMOUS VEHICLES

CYBERSECURITY: PROTECTING INDUSTRIAL CONTROL SYSTEMS

HOW INDUSTRIAL NETWORKING CAN PROVIDE SECURITY FROM DRONES
.webp)
Thermal Cameras Reveal How to Keep Your Home Cool During a Heat Wave

FLıR ONE PRO
.png)
Unmatched Maritime Awareness with Cooled Thermal Imaging
.png)
What Is the Right Handheld Thermal Camera for You?
.png)
Camera Resolution and Range
.png)
Special Applications for Marine Cameras
.png)
What’s The Difference between Thermal Imaging and Night Vision?
.png)
Can Thermal Imaging See Through Fog and Rain?

Which Cx-Series Camera Is Right for You?
.png)
What is MSX®?

Five Reasons Maritime First Responders Need Thermal Imaging
.png)
3 Distinguishing Features of Superior Thermal Cameras
.png)
Determine Which Visible and Thermal Security Cameras You Need

Bullet vs. PTZ vs. Dome: Which Security Camera Is Right for You?
Interfaces for Machine Vision
Machine Vision Sensor Review
.png)
Teledyne FLIR, the Industry Leader, Launches Boson +, a Long-Wave Infrared Thermal Imager Module with an Accuracy of Less Than 20 mK
.png)
Whitepaper: IP-Based Security Convergence
.png)
3 Technologies Transforming Safe Cities into Smart Cities
.png)
Insights from the Field: Ensuring Workplace Safety Using Thermal Camera Screening for Entry Control

Thermal Night Vision as a Force Multiplier

Can Thermal Imaging See Through Walls? And Other Common Questions
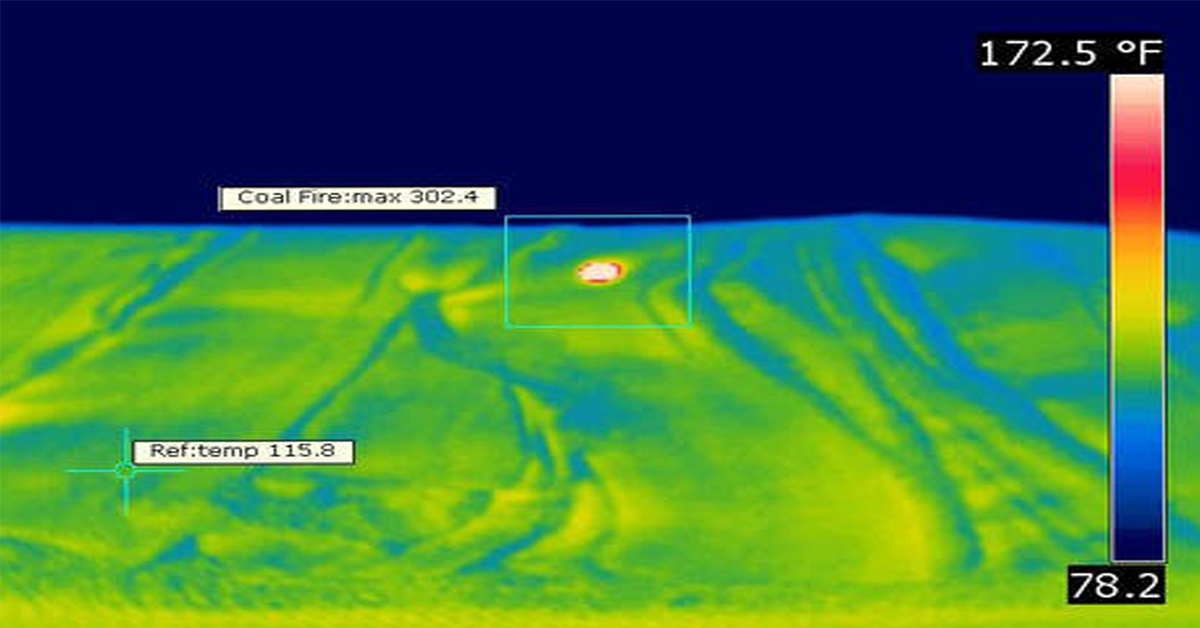
Application Spotlight: Early Fire Detection for Rapid Heat Generation

Protect Personnel and Equipment by Detecting Early Signs of Fire

Teledyne FLIR Launches A500f/A700f Cameras for Fire Detection and Condition Monitoring

Thermal Imaging Cameras Help Guarantee Fire Safety in Tunnels

Thermal Imaging Cameras Help to Prevent Fires

ITS-Series Dual AID Surpasses Standards for Fire Detection Systems in Japan

How Layering Multispectral PTZ Cameras and Radars Improve Perimeter Protection
POWER REMOTE RESET TECHNOLOGY - PRRT

Why Yacht Owners are Adding Thermal Imaging Cameras to Minimise the Risk of Lithium-Ion Battery Fires?
.png)
Intelligent Transportation Systems

Best Practices Guide for Perimeter Security Applications

Protect Pedestrians, Bicyclists and More with Thermal Smart Sensors

White Paper: Application of Ground-Based Security Radar to Perimeter Systems

What is Thermal Leakage and How to Reduce Its Risks

Battery Inspection Using Advanced Thermography

Providing ire Protection for Lithium Battery Storage

The Power of Thermal Imaging
.png)
Why Panel PCs Are Perfect For Industrial Applications?

Teledyne DALSA
.png)
Advantages of Virtual Barrier Video Analytics for Perimeter Security Systems
.png)
.png)
NASA Takes the Teledyne FLIR Boson Thermal Camera Module Out of this World
.png)
Port Security Enhancement: DP World Yarımca's Trust in FLIR Security Solutions for Effective and Safe Port Operations
.png)
The Importance of Thermal Sensitivity (NETD) for Detection Accuracy
.png)
Bosphorus Boat Show 2025: The Meeting Point of the Maritime World

Application Spotlight: Critical Asset Monitoring for Thermal Conditions
.png)
Thermal Imaging for Marine Firefighting

Imaging in Mobile Mapping
.png)
Using Thermal Imaging for Oil Spill Detection

Five Reasons Maritime First Responders Need Thermal Imaging

Case Study: Tackling Compressed Air Leaks in Automotive Parts Manufacturing with Acoustic Imaging

Thermal Night Vision as a Force Multiplier
.png)
Line Scan Contact Image Sensor - AxCIS

Beyond Resolution: What Really Makes a Camera System Work for Mobile Mapping
.png)
Multispectral Marine Cameras for USV Applications
.png)
Stabilizing FLIR Cameras for Smooth Viewing in Rough Waters
 (1).png)